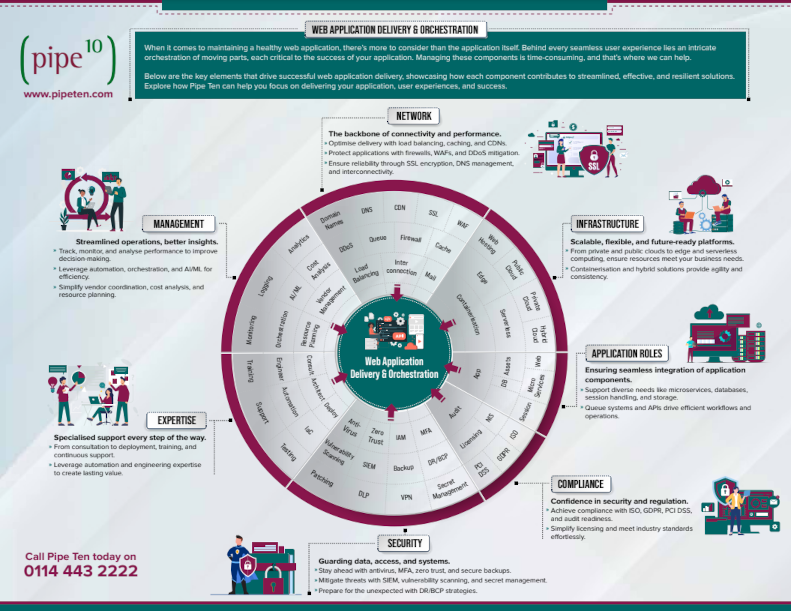
In today’s complex IT ecosystem, no single provider can be an expert in everything. We don’t claim to understand the nuances of endpoint fleet management any more than we’d expect you to be an expert in the intricacies of high-availability web application hosting.
At Pipe Ten, we specialise in delivering and orchestrating web applications, offering 24/7/365 expertise to ensure your clients’ platforms are available, fast, secure, and resilient. By partnering with us, you gain a trusted ally who manages the complexities of web infrastructure so you can confidently focus on delivering excellence in your core IT services.

When partnering with other Managed Service Providers, we know our performance reflects on your reputation. That’s why we prioritise clear communication, reliability, and consistent results, ensuring we meet your clients’ expectations every time.
Our focus on publicly-facing web application delivery complements your IT services. By partnering with us, you can ensure fast, secure, and reliable applications, preventing bottlenecks or downtime from impacting overall client satisfaction and trust in your other services.
Head of Service Delivery

Our MSP friendly services included:
- White-Label Expertise
- End-to-End Project Orchestration
- Full Stack Consultancy
- Cross-Platform Orchestration
Why choose Pipe Ten for your clients’ web application delivery?
- We speak geek
- Experts in web application delivery
- We care about user experiences
- Over Two Decades of Proven Success
- ISO27001, PCI DSS, Cyber Essentials Plus
- 24/7/365 Monitoring & Response
- Passionate, Expert, Continuous Support
- Global Reach, Delivered with a UK Touch
- Agile, Proactive, and Kaizen
Insights
CMA Public Cloud Report
The public cloud landscape is dominated by AWS and Azure, but other providers like DigitalOcean also play significant roles. This article explores a comparative analysis of AWS, Azure, and other cloud...
Insights
Ransomware Resistant Backup
In an age where data is as more precious than gold, protecting it from ransomware attacks is critical. Pipe Ten, as a managed services and backup provider, implements robust strategies to safeguard yo...
Insights
Over 20 years in the domain name industry
A crucial part of application infrastructure management is the Domain Name System (DNS). Offering reliable domain name registration and management services has been a cornerstone of Pipe Ten’s g...
More Insights
CMA Public Cloud Report
The public cloud landscape is dominated by AWS and Azure, but other providers like DigitalOcean also play significant roles. This article explores a comparative analysis of AWS, Azure, and other cloud...
Ransomware Resistant Backup
In an age where data is as more precious than gold, protecting it from ransomware attacks is critical. Pipe Ten, as a managed services and backup provider, implements robust strategies to safeguard yo...
Over 20 years in the domain name industry
A crucial part of application infrastructure management is the Domain Name System (DNS). Offering reliable domain name registration and management services has been a cornerstone of Pipe Ten’s g...